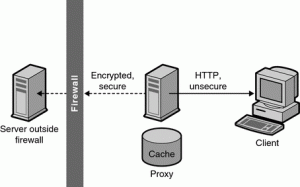
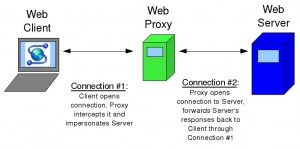
You can utilize a proxy server to stay unknown on the PC system. It implies that the proxy server that you utilize won’t uncover your unique IP (Internet Protocol) address. Through a proxy server, the customer reaches different administrations present on the system. The client interfaces with the server and after that the server demands for a specific page or document present on the system. In any case, it is not prescribed to utilize a proxy as different PCs on the system associate with your framework through IP address as it were.
While utilizing a site proxy server, you enter the URL that you need to visit in the space gave on the proxy site. The proxy site sends the solicitation for the page further to the source server and after that shows back the outcomes to your screen. This kind of server offered by Proxiesforent does not distinguish itself as proxy server and your IP location is not uncovered moreover.
You can likewise utilize “Anonymizers” with a specific end goal to stay unknown on the system. Ordinarily, these are paid administrations and the vast majority of them have their own interface that permits you to shroud you IP address. They give an abnormal state of secrecy yet the greater parts of them have some expense and are moderate in rate.
You can utilize certain product programs that shroud your IP address. These projects arrange and in addition deal with your setting so you can get to be unknown. By utilizing these product programs, you can undoubtedly sidestep certain settings in the event that in the event that you don’t have much information about intermediaries.
Many Technologies can likewise be executed to shroud your IP address. You can without much of a stretch cripple treats by utilizing the program choice. Thusly, sites won’t have the capacity to spare information on your PC. This can give a specific level of namelessness to the client.
For aggregate secrecy on the system, socks innovation can be utilized by the customer. Socks conventions are utilized as a part of this innovation in which a socks server demands and in addition retargets the information that is sent back. It gets to be difficult to figure the customer’s IP address as extraordinary socks conventions are actualized.
There are sure sorts of proxy servers such a straightforward, misshaping and high namelessness proxy servers that can be utilized to conceal your IP address. This is the way you would us be able to proxy server to stay unknown on the system.