Out of all the websites out there on the web to scrape, no other website is as complicated as Craiglist. This website is set up in such a way that the data is very hard to scrape off because of its API.
There are some sites that can scrape off the data with their API, but Craiglist is one tough website to come through. The API in Craigslist’s is set up differently. Instead of permitting you to extract data, Craigslist’s API is designed for people to post data. You can implement the API to post data in a bulk, but it isn’t made for pulling data.
This API might make you want to drop everything and give up, but it makes sense why Craigslist would set it up this way. After all, people who sell things in bulk often take up the site, so by allowing them to post in bulk, they save a lot of time.
Along with the API, Proxiesforent provides good proxies service. People have the ability to post ads no matter how many in number, and no matter what you are willing to sell, you have the ability and ease of doing so with the push of a button. Which is why the sites is one of the most popular when it comes to selling things over the internet.
Although it can get on your nerves and frustrate you, it really isn’t impossible to scrape data of craigslist. All you need to do is choose the right scraping service and then follow a few tips in order to complete the scraping process.
The first few things you need to do is choose a scraping service that will let you harvest all of the data you need from the site. While a few users chose to develop tools by their own stance, it is much easier to get a tool that is ready to go.
Of course, if you are skilled at web development, you can try your hand at it. Just remember that the API is basically backward, so you need to design your tool to work around that. Otherwise, it will be useless.
There is a huge amount of great options out there, but, of course, some stand out among the others. Let’s take a deep dive into a great free option and a quality paid option. Then, you can decide which one you prefer for your scrapping needs.
Proxy servers can dramatically improve performance for groups of users
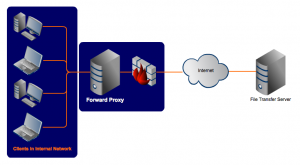
PROXY – A proxy act as an intermediary agent between its client and the server which they want to access, performing function directed towards a variety of purposes like security, caching etc.
As the name proxy, it means server which fills up or acts and provides functionalities of some other server.
PROXY SERVER – A server that sits between a client application, such as a Web browser, and a real server. It intercepts all requests to the real server to see if it can fulfill the requests itself. If not, it forwards the request to the real server.
A Proxy server is a computer that offers a computer network services to allow clients to make indirect connections to other network services.
It also acts as an intermediary between web server and its clients
A proxy server is a server , a computer system
Or application program that acts as an intermediary between clients
Seeking resources from other servers. A client connecting to the proxy server such as a file, connection, web page or other resources available from different servers.
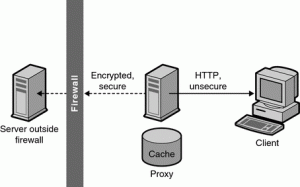
A proxy server may optionally alter the client’s request or the server’s response, and sometimes it may serve the request without contacting the specified server. In this case, it ‘caches’ responses from the remote server, and returns subsequent requests for the same content directly.
Proxy Server solves the problems of network congestion and slow response time and provides control over network resources without burdening end users or network administrators.
Proxiesforent provide best proxies in the world because this company provide better service like 24/7 live chat support
PURPOSES OF PROXY SERVER
Proxy servers have mainly two purposes:
Improve performance :
Proxy servers can dramatically improve performance for groups of users. This is because it saves the results of all requests for a certain amount of time. Consider the case where both users X and user Y access the World Wide Web through a proxy server. First user X requests a certain Web page, which we’ll call Page 1. Sometime later, user Y requests the same page. Instead of forwarding the request to the Web server where Page 1 resides, which can be a time-consuming operation, the proxy server simply returns the Page 1 that it already fetched for user X. Since the proxy server is often on the same network as the user, this is a much faster operation. Real proxy servers support hundreds or thousands of users. The major online services such as America Online, MSN, and Yahoo, for example, employ an array of proxy servers.
Filter Requests:
Proxy servers can also be used to filter requests. For example, a company might use a proxy server to prevent its employees from accessing a specific set of Web sites.
WORKING OF PROXY SERVER
The proxy server evaluates the request according to its filtering rules. For example, it may filter traffic by IP address or protocol. If the request is validated by the filter, the proxy provides the resource by connecting to the relevant server and requesting the service on behalf of the client.
Proxy sites enable you to bypass your own Internet provider and browse through the proxy web site. All that you have to do is type the website address you would like to visit in the form they provide and start browsing. Once you keep browsing using that form, you are protected and your real IP address is not being logged.
Once you have configured your web browser as described, your browser will load a CGI script each time it is restarted. This script redefines the function that determines how to fetch the URL that is being requested. If the URL matches a pattern or a site that requires a proxy, it will connect to the proxy server rather than going directly to the site.
Step 1: User starts browser, connects to proxy server to get the Proxy
Automatic Configuration (PAC) file.
fetch request: proxy.ucla.edu/cgi/proxy
+—–+ +—–+
| U | | P |
| S | ==================>| X |
| R | | Y |
+—–+ +—–+
Step 2: Proxy server returns “proxy”, which configures
browser to do proxying.
+—–+ +—–+
| U | “proxy” loaded | P |
| S |<================== | X |
| R | | Y | +- +—–+ +—–+
Step 3: User requests URL, URL compared against function retrieved from “proxy”, connection route is determined.
Step 4a: Route for URL returned from function is “DIRECT”(no proxy required). Browser retrieves URL directly. (*Note: At this point, every URL returns “DIRECT” unless it is one that is know to restrict access to ucla.edu*)
+—–+ +—–+
| U | fetch URL | S |
| S |<==================>| R |
| R | | V |
+—–+ +—–+
Step 4b1: Route for URL returned from function is “PROXY xxxxx ” (proxy required). Browser contacts proxy server and requests page.
+—–+ +—–+ +—–+
| U | request URL | P | | S |
| S | ==================>| X | | R |
| R | | Y | | V |
+—–+ +—–+ +—–+
Step 4b2: Proxy contacts server and requests page.
+—–+ +—–+ +—–+
| U | | P | request URL | S |
| S | | X | ==================>| R |
| R | | Y | | V |
+—–+ +—–+ +—–+
Step 4b3: Server sees request from ucla.edu domain (proxy address ) and returns URL to proxy.
+—–+ +—–+ +—–+
| U | | P | return URL | S |
| S | | X |<================== | R |
| R | | Y | | V |
+—–+ +—–+ +—–+
Step 4b4: Proxy returns URL to User.
+—–+ +—–+ +—–+
| U | return URL | P | | S |
| S |<================== | X | | R |
| R | | Y | | V |
+—–+ +—–+ +—–+
TYPES OF PROXY SERVER
There are many different types of Proxy Servers out there. Depending on the purpose you can get Proxy Servers to route any of these common protocols, and many more ;
FTP Proxy Server:
Relays and caches FTP Traffic.
HTTP Proxy Server:
A one-way request to retrieve Web Pages.
Socks Proxy Server:
A newer protocol to allow relaying of far more different types of data, whether TCP or UDP.
NAT Proxy Server:
This one works a little different, it allows the redirection of all packets without a Program having to support a Proxy Server.
SSL Proxy Server:
An extension was created to the HTTP Proxy Server which allows relaying of TCP data similar to a Socks Proxy Server. This one has done mainly to allow encryption of Web Page
requests.
Caching proxy server:
A caching proxy server accelerates service requests by retrieving content saved from a previous request made by the same client or even other clients. Caching proxies keep local copies of frequently requested resources, allowing large organizations to significantly reduce their upstream bandwidth usage and cost, while significantly increasing performance
Web proxy :
A proxy that focuses on World Wide Web traffic is called a “web proxy”. The most common use of a web proxy is to serve as a web cache.
Furthermore, a Proxy Server can be split into another two Categories:
Anonymous:
An Anonymous Proxy Server blocks the remote Computer from knowing the identity of the
A computer using the Proxy Server to make requests.
Transparent:
A Transparent Proxy Server tells the remote Computer the IP Address of your Computer. This provides no privacy.
Functional Modules
Proxy User Interface :
This Module is responsible to control and manage the User Interface. It will provide the user with an easy to use GUI, a window with the menu.
The menu options should provide commands to perform the following functions:
Start Proxy
Stop Proxy
Exit
Blocking URL
Blocking Client
Manage Log
Manage Cache
Modify Configuration
Proxy Server Listener :
The main function of the proxy starts here. This module will serve as a Port listening to clients i.e. page requests from a web browser. It will create a new connection for each request from the clients. One more important feature of this module would to block clients which are there in the blocked list given by the user.
Connection Manager
This module will contain the main functions of the Proxy Server. It will read the request header from the client. It will parse the URL and determine whether the URL is blocked or not. Else it will generate a connection to the web server. Then it will read the reply header from the web server. If there is no copy of the page in the cache then it will download the page from Web Server else will check its last modified date from the reply header and accordingly will read from the cache or serve from the Web. Then it will also check the header for caching allowed or not and accordingly will cache the page.
Cache Manager :
The Cache Manager is responsible for storing, deleting, clearing and searching of web pages in the cache.
Log Manager :
The Log Manager is responsible viewing, clearing and updating the Log.
Configuration :
This module will enable the user to make his configuration settings. It will work with the other modules to perform the desired configurations such as caching (on/off), log (on/off), etc.
Small Data and Big Data
If you’re wondering what Small data is, it is basically data in a volume and a format that makes it accessible, informative and actionable.
The Small Data Group offers the certain explanation to how Small Data Functions. It connects people with time to time, meaningful insights or views which are organized and packaged that are often visually accessible, can be understood, and actionable for day to day tasks.
The term small data stands in divergence with big data, and usually refers to a blend of structured and unstructured data that may be measured in petabytes or exabytes.
Big data is often said to be designated by the 3Vs that are (1)the volume of data, (2)the variety of types of data and (3)the velocity at which it is processed, all of which combine to make big data very difficult to manage. Small data, in difference, consists of usable bits.
The idea of big data is enthralling.If you wish to uncover hidden patterns about customer behavior, predict the next election, or see where to focus ad spend, There’s an application for that. And to listen to the Indian pundits, we should all be telling our kids to become scientists of data, since every company will need to hire an army of them to survive the next wave of digital disruption.
The idea of small data is that businesses can get busy and a lot of work may come in, results without getting the kinds of systems commonly used in big data analytics. A company might invest in a large amount of server storage, and use proper tools for analytics machines the time and date of the actions made by users, demographic informational data and much more. All of this might get filtered into a central data warehouse.
Reverse Proxy Functioning
A reverse proxy is mostly a server-side concept, and is usually used in the context of (CDNs) Content Distribution Networks for caching static HTTP content. A forward proxy is usually a client side concept used for anonymity, to subvert censorship, and as a web accelerator.
For example you have a single web server,and need to serve static HTML pages to your clients very quickly. However, you are running WordPress, Joomla, or some other dynamic content management system. Every time someone visits the homepage of your website, your server has to spend time regenerating the page for every user.
A reverse proxy server is a type of buy proxy server that typically sits behind the firewall in a private network and directs client requests to the appropriate back-end server. A reverse proxy provides an additional level of abstraction and control to ensure the smooth flow of network traffic between clients and servers.A server-side reverse proxy would be used in this context to cache static content, like images, CSS, and static HTML. You could even use multiple reverse proxy servers to balance the load. If you are willing to pay, CDNs can cache your site across multiple geographic locations. Another popular use of reverse proxies is for ‘transparent’ HTTPS. Rather than load and setup every webserver with an SSL certificate, single a reverse proxy can sit in front of all the webservers, to encrypt and serve to clients over HTTPS. Usually, transparent HTTPS reverse proxy servers have dedicated hardware for SSL acceleration.
A reverse proxy is a proxy configured to handle requests from a group of remote or arbitrary clients to a group of known resources under the control of the local Administrator. An example of this is a load balancer also known as Application Delivery Controller that provides application high availability and optimization to workloads such as Microsoft Lync, Exchange and SharePoint. The purpose of a reverse proxy is to manage the server systems.
Uses of a reverse proxy:
* Load Balancing
* Web Acceleration and
* Security and anonymity
Three Reasons For Starting a Proxy
Proxies are utilized for two reasons. Firstly, by utilizing a proxy webpage, you can get to sites that are obstructed from being gotten to at your area. Besides, proxies are utilized to keep your data private. There are sites that log your IP address. At the point when these sites do this, your security and your own and searching data may be traded off. Proxies can deal with that for you by keeping the sites that you are perusing from identifying your genuine IP address.
Since there are increasingly individuals who are finding the benefits of utilizing proxies, sooner or later, your most loved proxy will get to be temperamental or the system director will find that you are utilizing that proxy and will likewise obstruct that site. In light of these issues with utilizing an outsider proxy, it may regard begin your own particular free proxy administration.
1. You can foresee the dependability of your proxy
Since you are the proprietor of the proxy, you know about any specialized issues that your proxy needs to address. You can break down the measure of transfer speed that your proxy site is utilizing and you can think of routes on the best way to set up your proxy with the goal that it utilizes less of the server assets. As the executive, you have a proxy that is prepared to utilize when you require it.
2. You can procure some wage through commercials, referrals and enrolment
This is the thing that most free proxy heads do. If you host been utilizing third-gathering proxy administrations for quite a while, you will see that large portions of them have promotions. There are some that offer flag space, while others use Google AdSense as their wellspring of income.
You can likewise do those with your free proxy. That way, you can likewise get some salary while putting time and cash in keeping up the proxy.
3. It is – well, nearly
At first, you will need to spend some money for getting the space and the facilitating. You may likewise need to pay for the proxy script. In any case, once everything is up and running, it wouldn’t cost you to such an extent. Actually, if you as of now have your own facilitating account, then (if your web host bolsters it) you can simply include the proxy.
If you have chosen to have your own particular proxy, remember that setting up and dealing with an proxy will require some specialized skill. There are some aides on the Internet on the best way.
Can You Use a Secure Proxy Server to Improve Your Security?
One approach to ensure you online when surfing the web is by utilizing a safe proxy server. However, simply picking any proxy to utilize is not prudent, as you may pick one that is not secure and rather than your surfing being unknown your data may very well be being sent elsewhere, which can make this a terrible circumstance for you. More the world and particularly the web are loaded with individuals why holding should up take your personality.
Pitiful yet genuine, the dangers for these cheats are so insignificant contrasted with any ordinary wrongdoing and even decreases when they set themselves up in a nation with careless web laws and with a legislature that can’t police the circumstance.
One of the fundamental and most critical issue while surfing the web is that most data is moved in effortlessly discernable arrangement, called ascii content. So essentially all data that leaves your PC and goes over the web can be in a flash caught and read by any individual who does as such.
Every last day a large number of individuals utilize these proxies by Proxiesforent and accidental to all of them their information is being captured and read. With a server designed to store mode and empowering programming these web privateers can record everything … your usernames, account logins and passwords, your Visa points of interest, standardized savings number, and so on and they have your data.
You have most likely heard the colloquialism … “there is no such thing as a free lunch”, well that remains constant with free intermediaries too. The expense to run a free proxy server is exceptionally costly, so why might they need to give them away allowed to general society? The answer here is quite basic, it is one of two reasons … #1 being that somebody, more than likely an organization did not close every one of the ports to their proxy server or … #2 it has been finished by somebody intentionally to make a trap to take individuals’ information
Actually it is unknown how to see if a legitimate organization is running an proxy server or if it was programmers, however there is a decent protection programming out available now that will permit you to surf and purchase securely on the web. You will have admittance to a huge system of private intermediaries to utilize; the project itself is quick and totally encoded, permitting you effortless surfing.
Proxy Servers to Safeguard Computer Networks
The misuse of opportunity is verging on inescapable in today’s reality. As a check, a considerable measure of confinements must be placed set up to protect certain qualities consequently, practically making a joke of our well-deserved flexibility. Most likely, the human instinct is extremely exploratory, courageous and brave. This maybe could clarify the failure of specific people to take after lawfulness or carry on in an effectively unsurprising or craved.
Trespassing is a wrongdoing innate to people subsequently, the requirement for laws and measures to secure private property to be ordered.
In the internet, trespassing still represents a noteworthy issue. The undesirable or unapproved utilize or mishandle of private or open systems has justified the work of proxy servers to shield these systems. As it is the tradition, each arrangement makes another issue thus the issue emerges where the proxy server pieces or channels even substance of sites that doesn’t represent any risk to the security of the system.
While the system proprietors may be advocated in controlling or restricting access to their system, clients can simply discover destructive or innocuous motivations to need to bypass this control. Whatever your reasons are, you are in charge of your activities.
Since some proxy servers just sift through undesirable or unapproved activity and just framework heads can change these settings; to have the capacity to get to the vast majority of this system, free proxy servers is an exceptionally normal approach to take.
A web pursuit will uncover that there are some free proxy servers sites that give courses (codes) to sidestep generally channels. At the point when perusing from these destinations, one can visit any locales at whatever point they need with no limitations. It likewise permits an unknown client to peruse the web safely – individual and private data that is shared over the net is encoded.
The site likewise concedes one unlimited access to sites that are for any reasons obstructed by school, work, or nations system and so on. The strides are exceptionally basic:
• Open any web program and hunt down free proxy servers. If you are going to pass individual data to this server, you should ensure that is facilitated by proprietors with known trustworthiness else, you run a danger of having your information blocked.
• When you locate a suitable one, sort the web location of the blocked webpage you are attempting to access into the space gave and enter.
• This takes you to the page that you are attempting to get to.
What You Must Know About Automatic Proxy Changers
A programmed proxy changer is viewed as a completely need for those that get a kick out of the chance to surf the Web secretly. The reason is that regardless of the fact that you locate a quick server today, there is no insurance that it will in any case work in the following couple of days. Actually there is no certification it will even be available the following day.
To get around this issue, you require a project that can change the servers you utilize, however it will likewise must be a great deal more than that. Case in point, many individuals utilize these mysterious servers to circumvent the Net, yet a programmed proxy changer that is perfect with an email program or with visit programs like MIRC means you will have the capacity to utilize them with the same level of secrecy that surfing the Web does.
The reason for changing servers obviously, is to offer you some assistance with finding one that is working. Given that certainty, you ought to search for programming that has broad inquiry and alteration highlights. Other than the typical inquiry capacity, it must have the capacity to invigorate its rundown, build a progression of servers you can utilize, and decide the kind of server that it has recognized, whether it is SOCKS or http, or some other sort.
The term programmed does not simply apply to the time when the server can be changed, yet it should likewise have the capacity to modify it at whatever point the present one impedes. Likewise, similarity will be an issue; it need not have the ability to cross stages, but rather in the event that you can utilize it with various programs from Proxiesforent, which are shockingly, better. Some additionally can work with different projects that demonstration like doors or firewalls. These are components that system supervisors will search for.
Something else that you will need to search for will be its sifting abilities. A programmed proxy changer that is very much planned will be fit for tolerating or dismissing treats, dispense with advertisements, consequently uprooting the substance of a brief organizer and that’s only the tip of the iceberg.
In the event that you need to deal with your system or simply have a more secure time when you are on the web, this application is fundamental. Some are free, others will require an expense. Be that as it may, whichever you pick, simply make sure that every one of the components you need arrive and with no unnecessary elements that will simply obstruct your framework.
Why Should You Get Anonymous Proxy Service?
Have you ever asked why numerous individuals get mysterious intermediary administration? This is not being neurotic or over the top about your security, but rather actually giving without end your IP location is similar to giving endlessly your place of residence to a complete outsider! We don’t do that; so why would it be a good idea for us to give anybody a chance to have our IP address?
The truth of the matter is that law ensures everybody against fraud yet in the meantime permits unsecured locales to get our IP addresses. A few programmers abuse this data. What really happens is that when we visit a site or a discussion and so on an IP log is made which is required to be kept secret. In any case, there are occasions when the website admins of these locales abuse these logs which they shouldn’t utilize and make individual data open.
Although such infringement can be managed lawfully however that would mean spending a lot of cash to document a claim against the site and as a rule these locales are situated in remote nations and they don’t have comparative laws to ensure your data, other than the harm has as of now been finished. In such cases it is ideal to safe than too bad.
You will discover a great deal of good administration suppliers like Proxiesforent which give unknown intermediary administrations diverse levels of security and obscurity. The inquiry why you ought to keep your web surfing without a follow is imperative in light of the fact that there are numerous organizations who offer cash to website admins of various gatherings and sites to offer the information of clients in view of their areas. The other explanation behind concealing your IP is to shield yourself from being followed by anybody as programmers can track your action and at times they can misuse this data.
In the event that you are searching for making your web surfing untraceable then the best arrangement is to get on a virtual private system otherwise called VPN. Along these lines you can keep on surfing the web unreservedly without having the apprehension of being followed or hassled by anybody later.
Just to include as a note of alert. In the event that your exercises on the web are unlawful then these administration suppliers won’t shield you from the law. Presumably they will give all your movement information to the powers. So this is no real way to cover your strides on the off chance that you are perpetrating a wrongdoing on the web, yet a support of shield you from different guilty parties.
Proxy Allows Anonymous Surfing
Online security and the office of mysterious using so as to surf is an aid conceded a Proxy. When you are working in the solace of your home or office, why do you need namelessness? Since the Internet is not a mysterious spot. Aside from the infections, bugs, spyware, adware and so on slinking in the internet, which can harm your PC, your web exercises are additionally seen by snoopers.
For Anonymous Surfing, before you begin skimming, ensure that against infection programming is introduced, and firewall has been empowered. Presently, you are prepared to scan, namelessly, securely and with security. Utilized, a proxy permits unknown surfing. The Internet has a lot of free intermediaries. In any case, paid administrations can bring more fulfilment while skimming. More than anything, a paid administration will imply that you are more secure, in light of the fact that your data is encoded, and nobody can get to it.
Encryption implies your data trade can’t be snooped upon. While transmitting data, to guarantee security encryption utilizes unique PC calculations, which are continually changed, so that nobody gets what you are trading.
Contrasted with a free Proxy, it is constantly better to go for a paid proxy which permits unknown surfing. Be that as it may, on the grounds that you paid for an administration does not as a matter of course mean it’s a superior Proxy. How then, will you detect an impeccable proxy which guarantees wellbeing and security? Are there any approaches to guarantee that you are being offered the best of security? You can keep an eye on this through two or three basic things, with the goal that you are guaranteed that your proxy is alright.
In the event that it has a long standing notoriety, you can trust it. There are various situations when intermediaries are discovered today, however vanish the following day. This is something you should observe. Furthermore, you should know from where the proxy is working. There are a couple places on the planet which keep on denying offering your data to others.
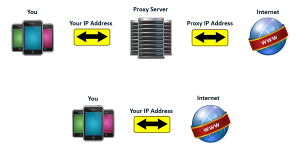
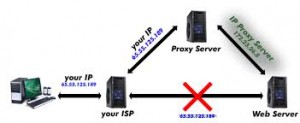
Proxy servers shroud your IP address. Web Protocol location is a novel number given to just you. Likewise, every PC with web availability will have a remarkable IP, given by their administration suppliers. Proxy servers permit mysterious surfing, as your character is covered up even as you peruse. Regardless of the fact that somebody gets hold of the IP way of life as you search, it is just the proxy’s IP, and not yours.